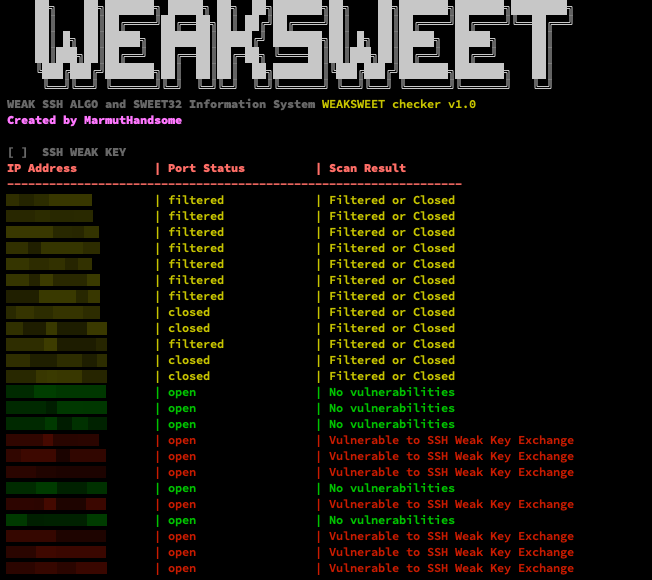
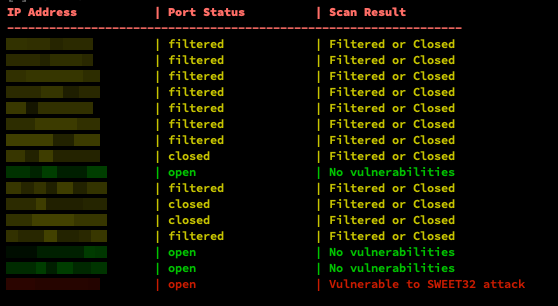
WEAKSWEET Checker is a Bash script that scans a list of IP addresses for weak SSH algorithms and vulnerabilities related to the SWEET32 attack. It provides a comprehensive report of the scan results.
- Clone the repository or download the Bash script (
weaksweet.sh) to your local machine:
git clone https://github.com/nieshakenzie/WeakSweet.git- Go to directory WeakSweet:
cd WeakSweet- Make the script executable:
chmod +x weaksweet.shTo scan a list of IP addresses for weak SSH algorithms and SWEET32 vulnerabilities, use the following command:
./weaksweet.sh -i input_file.txt -o output_file.txtReplace input_file.txt with the path to your input file containing a list of IP addresses.
Replace output_file.txt with the desired name of the output file where the scan results will be saved.
-h: Display the help message, which includes usage instructions and available options.
-i input_file: Specify the input file containing a list of IP addresses to scan. Each IP address should be on a separate line in the file.
-o output_file: Specify the output file where the scan results will be saved. If not specified, the default output file is output.txt.
Here is an example of the output format generated by WEAKSWEET Checker:
IP Address | Port Status | Scan Result
---------------------------------------------------------
192.168.1.0 | open | Vulnerable to SSH Weak Key Exchange
192.168.1.1 | open | No vulnerabilities
192.168.1.2 | closed | Filtered or Closed
Output File Saved on output.txt