Greetings my fellow Technology Advocates and Specialists.
| USECASE INTRODUCTION:- |
|---|
| Azure Key Vault is Protected by "Access Policies" and "Firewall and Virtual Networks". An Azure Cloud Engineer Cannot Fetch Secrets because of one of the condition or both (Depending upon the Scenerio). |
| PROBLEM STATEMENTS:- |
|---|
- User Account of Cloud Engineer is not part of Key Vault Access Policy. Hence Secrets cannot be viewed from Azure Portal.
- Key Vault is Protected by Organization's Public NAT IPs. Secrets cannot be viewed from Azure Portal unless Cloud Engineer is working from inside Organization Network.
- Key Vault is Protected by Azure Virtual Network. Secrets cannot be viewed from Azure Portal unless inside Azure Virtual Network.
| QUESTION TIME:- |
|---|
| How will the Cloud Engineer Fetch Secrets ? |
| LIVE RECORDED SESSION:- |
|---|
| LIVE DEMO was Recorded as part of my Presentation in WELSH AZURE GROUP Forum/Platform |
| Duration of My Demo = 32 Mins 38 Secs |
| Start and End Time = 00:39:22 to 01:12:00 |
 |
|---|
| REQUIREMENTS:- |
|---|
- Azure Key Vault
- Three Sample Secrets in Azure Key Vault
- Azure Resource Manager Service Connection
- Azure DevOps Pipeline (YAML)
| NOTE:- |
|---|
The Service Principal (which is required to Create Service Connection) should at minimum have GET and LIST Access Policy Permissions in Azure Key Vault.
| BELOW DISPLAYS THE SAMPLE SECRETS IN KEY VAULT:- |
|---|
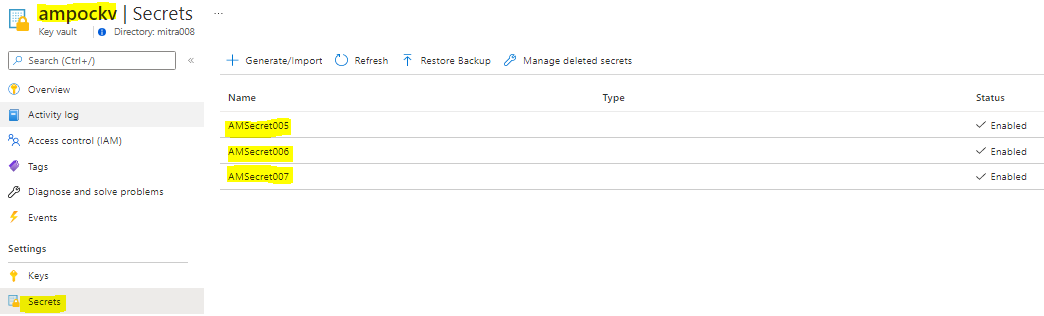 |
| WHAT DOES THE PIPELINE DO:- |
|---|
| # | PIPELINE TASKS |
|---|---|
| 1. | AZURE KEY VAULT TASKS |
| 2. | FETCH ALL SECRETS AND STORE IT IN A TEXT FILE |
| 3. | COPY THE SECRETS TEXT FILE TO ARTIFACTS STAGING DIRECTORY |
| 4. | PUBLISH THE ARTIFACTS |